The main ethos of this blog is showcasing the ability to build enterprise-level infrastructure in Azure as a small business – without breaking the bank and having to manage hardware. With this in mind, Azure Virtual Network Gateway is one of the most effective ways to quickly set up a VPN for users to connect to Azure infrastructure. As we transition to a post-pandemic world, I have a number of friends who work for organizations with no traditional offices and all infrastructure in public clouds – the key piece for enabling end-user connectivity to cloud-hosted infrastructure is a solid VPN, and setting up an Azure AD virtual network Gateway
What are we going to do:
- Create a Virtual Network Gateway
- Grant Admin consent to the Azure VPN Enterprise App
- Configure Point-to-site VPN
Create a Virtual Network Gateway in Azure
- Navigate to Virtual Network Gateway Portal (https://portal.azure.com/#view/HubsExtension/BrowseResource/resourceType/Microsoft.Network%2FvirtualNetworkGateways)
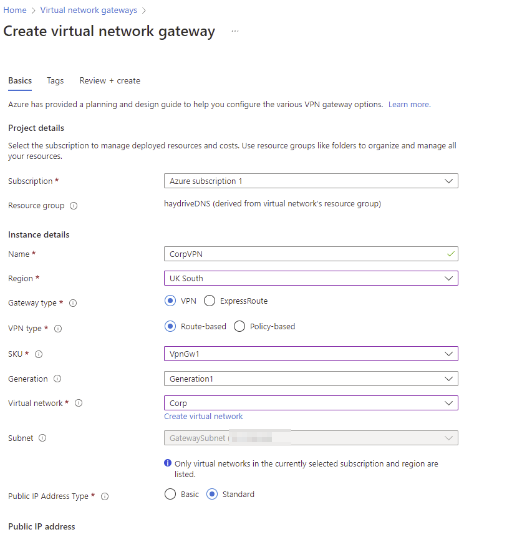
- Select the option to Create a gateway and populate the information
- Review settings and create the gateway
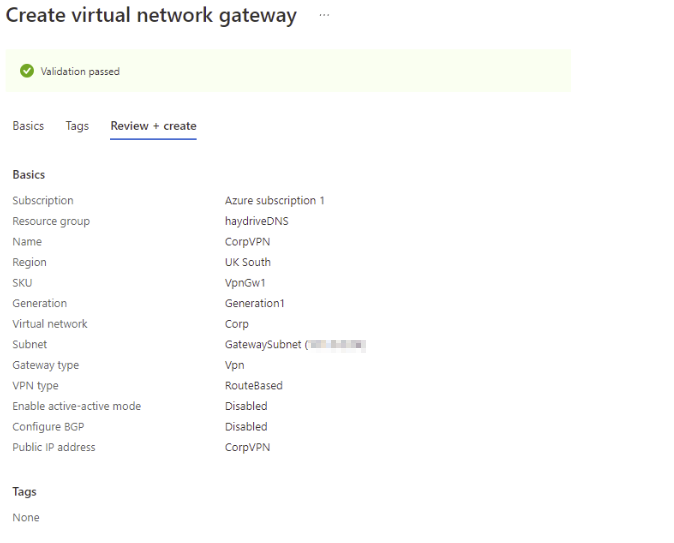
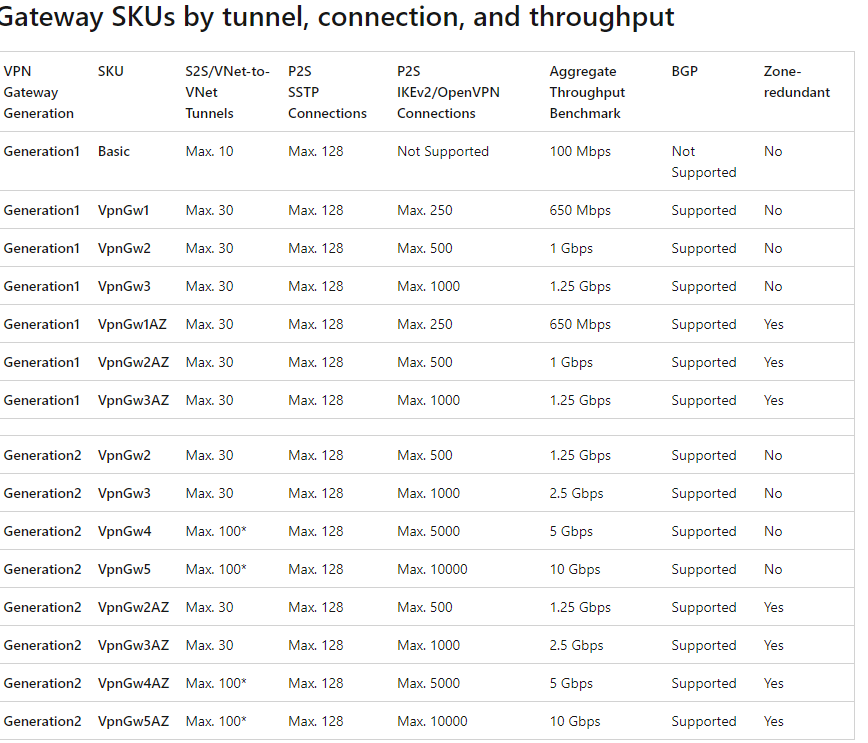
Since this is to connect users to our azure network only, we are selecting the following options – VPN Gateway, Route-Based, and a VpnGw1 SKU. Pricing information can be found here ( About Azure VPN Gateway | Microsoft Docs) but for the purpose of my testing, the joining of a windows 10 device to my Azure AD DS Managed domain the SKU I have chosen is the cheapest option that will enable me to create a point-to-site VPN connection.
Grant Admin consent to the Azure VPN Enterprise App
Once the Virtual Gateway has been created we need to Grant Admin consent to the Azure VPN Enterprise App, the Azure VPN app will be used by our end-users for connecting to the VPN. App consent for the Azure VPN application can be granted using this link: https://login.microsoftonline.com/common/oauth2/authorize?client_id=41b23e61-6c1e-4545-b367-cd054e0ed4b4&response_type=code&redirect_uri=https://portal.azure.com&nonce=1234&prompt=admin_consent
For the admin consent, we need an account with global Admin Permissions on the tenant. And consent can be granted by clicking accept on the admin request view below:
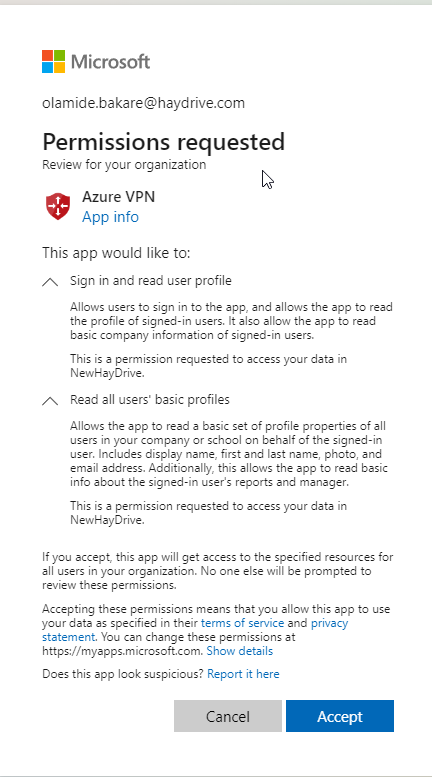
Once this has been accepted, the Azure VPN application should now be listed in your list of Enterprise Apps (Enterprise applications – Microsoft Azure).
CONFIGURE POINT TO SITE VPN
Once admin consent for the Azure VPN app has been granted, we can go ahead and configure our point-to-site VPN:
- To configure a Point-to-site VPN we first need to take note of our Azure AD tenant ID, which can be found on the Azure AD tenant’s properties page https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Properties
- Navigate to the Gateway in Azure,
- Under settings, select Point-to-Site configuration, then Configure now
- Point to Site configuration
- Select Tunnel type as OpenVPN(SSL)
- Set Authentication type as Azure Active Directory
- Enter Audience (which is the application ID below for the Azure VPN Enterprise App )
41b23e61-6c1e-4545-b367-cd054e0ed4b4 for Azure Public
- Specify Tenant, in the format below
https://login.microsoftonline.com/INSERTtenantID
- Specify issuer in the format below with a trailing /
https://sts.windows.net/INSERTtenantID/
- Click Save
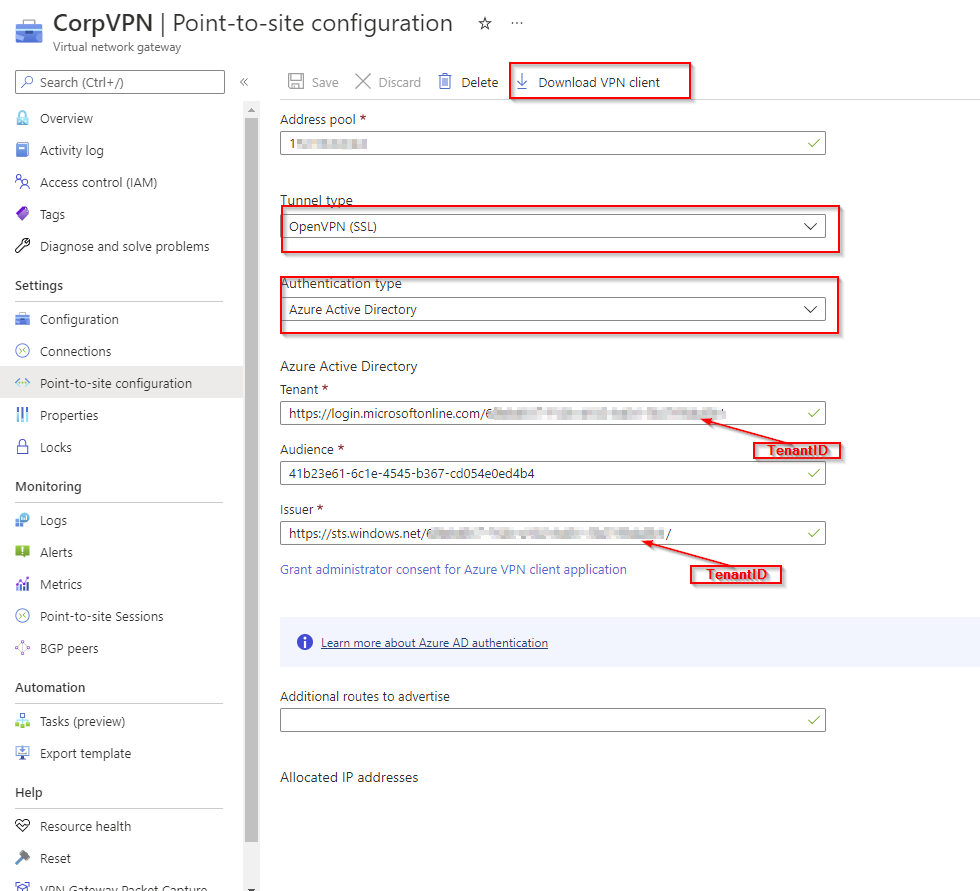
- After saving, download the VPN client
The downloaded VPN client will give us the XML file which we will provide to users for connecting to the VPN using the Azure VPN client we registered earlier. See the blog here ( https://haydrive.com/connecting-to-an-azure-vnet-gateway-point-to-site-vpn-using-the-azure-vpn-client/) for connecting to the VPN and installing the Azure VPN client.
Sources: