I recently had a requirement to upgrade BitLocker encryption method for our devices from AES 128-bit to AES 256-bit to meet compliance requirements. Currently, using the tools we have within the org ( Intune, Group Policy, Manage Engine) there is no straightforward way to make this happen automatically without some creativity. So to make this change, a process was developed using a combination of Intune’s Proactive Remediation functionality ,a couple PowerShell scripts and a configuration profile in Intune. To achieve our requirement we essentially need to Decrypt the device, then re-encrypt using the desired method.
While this process is being used specifically for upgrading to AES 256-bit , it can be used for any situation where we need to make changes to BitLocker polices that requires the device to be decrypted first.
Steps:
- Decrypt device using a Proactive remediation package
- Re-encrypt using a configuration profile in Intune
Pre-reqs:
- Device enrolled into Intune and Endpoint Analytics
- Windows 10/11 device managed by Intune
Decrypt Device Using Proactive Remediation
To decrypt the device we are using a proactive remediation package , this runs 2 PowerShell scripts to detect the current encryption mode, and if it matches the older method (AES 128) a remediation script is then deployed to decrypt the device.
Detect the current encryption Method:
$bitlocker= Get-BitLockerVolume | select EncryptionMethod
$bitlockerEnxryptionMethod = $bitlocker.EncryptionMethod
$oldMethod = “128”
if ( $bitlockerEnxryptionMethod -ccontains $oldMethod ) {
Write-Host “Device is currently XtsAes128”
Exit 1
} else {
Write-Host “Device is currently $bitlockerEnxryptionMethod”
Exit 0
}
The write-host in the script above is used to populate the “Pre-remediation detection output” field. which can be used to verify the encryption method and track the progress of this operation.
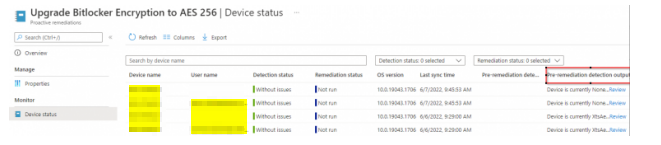
IF the current encryption matches 128, the remediation script is ran to decrypt the device.
$BitlockerVolume = Get-BitLockerVolume
Disable-BitLocker -MountPoint $BitlockerVolume
this command decrypts the bitlocker volume
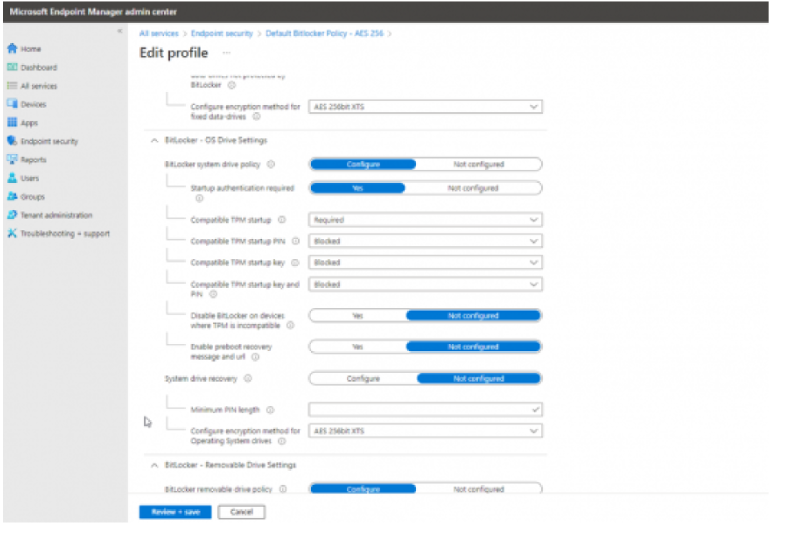
Re-encrypt using a configuration profile in Intune
Once the device has been decrypted via the proactive remediation package we can get Intune to re-encrypt the device at the desired method using a configuration profile.
Because we have created the detection policy to report out what the current encryption method of the devices are – we can use the reporting section to track the success of this activity. I know that we can obviously achieve the decryption/re-encryption using a complete PowerShell script to accomplish the entire objective – but using proactive remediation and Intune to implement this gives us additional reporting and tracking benefits.
Deployment:
To make the deployment process smooth I simply
- Created a security group called Win10-Bitlocker-256
- Excluded Win10-Bitlocker-256 from the current BitLocker policy in Intune
- Deployed my proactive remediation package/Policy to Win10-Bitlocker-256
- Deployed the new policy for AES 256-bit encryption to Win10-Bitlocker-256
By doing it this way, I can be sure that as soon as I drop a device into the Win10-Bitlocker-256 group the the device can get all the necessary policies applied and there is only one group for the IT Operations/frontline team to manage.
User experience and summary:
One of my main concerns doing this was regarding what the experience looks like for the end-user , while I do not have screenshots of user experience in this write-up , the general feedback has been that the user barely notices the activity as it happens mostly silently and in the background.
This was a very quick solution to a problem we had to fix very quickly to meet a compliance objective, while there might be other ways to achieve the same end, for an organisation with Intune enrolled devices and with the license to utilise proacive remediation , this was an optimum solution for us.
If you are reading this and can think of a much better way to do this or want to talk Intune/device management feel free to contact me via o.bakare@haydrive.com
Sources:
https://docs.microsoft.com/en-us/mem/analytics/enroll-intune
https://docs.microsoft.com/en-us/mem/analytics/proactive-remediations